OpenVPN and VisionSOM-6ULL: Difference between revisions
From SomLabs Wiki
Anna Kubacka (talk | contribs) No edit summary |
No edit summary |
||
| (7 intermediate revisions by 2 users not shown) | |||
| Line 2: | Line 2: | ||
__FORCETOC__ | __FORCETOC__ | ||
''OpenVPN'' [1] is an open-source software application that implements virtual private network (VPN) techniques to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. In other words, ''OpenVPN'' allows you to create a private network over the public Internet and tunnels your network connection securely. This tutorial describes the steps to setup | ''OpenVPN'' [1] is an open-source software application that implements virtual private network (VPN) techniques to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. In other words, ''OpenVPN'' allows you to create a private network over the public Internet and tunnels your network connection securely. This tutorial describes the steps to setup the ''OpenVPN'' server on ''VisionSOM-6ULL'' module. | ||
== Prerequisites == | == Prerequisites == | ||
This tutorial based on | This tutorial is based on a pre-prepared image for VisionSOM-6ULL module. The image is available here: [http://ftp.somlabs.com/VisionSOM-6ULL/SoMLabs-VisionSOM-6ULL-OpenVPN.zip SoMLabs-VisionSOM-6ULL-OpenVPN.zip]. | ||
For testing purposes user '''root''' has a password '''somlabs'''. | |||
Then you need to write the image file to microSD card. More information you can find in manuals: [[How to prepare SD Card with Debian 9.2 for VisionSOM-6ULL on Linux]] or [[How to prepare SD Card with Debian 9.2 for VisionSOM-6ULL on Windows]]. Please remember to use a proper image file: [http://ftp.somlabs.com/VisionSOM-6ULL/SoMLabs-VisionSOM-6ULL-OpenVPN.zip SoMLabs-VisionSOM-6ULL-OpenVPN.zip]. | |||
== Kernel configuration – TUN/TAP device support == | == Kernel configuration – TUN/TAP device support == | ||
| Line 38: | Line 42: | ||
''OpenVPN'' package – which is available in Debian's default repositories - provides both server and client mode. To update server's package repository and install ''openvpn'' software: | ''OpenVPN'' package – which is available in Debian's default repositories - provides both server and client mode. To update server's package repository and install ''openvpn'' software: | ||
root@somlabs:~# '''apt-get update''' | |||
root@somlabs:~# '''apt-get install openvpn''' | root@somlabs:~# '''apt-get install openvpn''' | ||
Reading package lists... Done | Reading package lists... Done | ||
Building dependency tree | Building dependency tree | ||
Reading state information... Done | Reading state information... Done | ||
The following additional packages will be installed: | The following additional packages will be installed: | ||
easy-rsa libccid liblzo2-2 libpcsclite1 libpkcs11-helper1 libusb-1.0-0 opensc opensc-pkcs11 openssl pcscd | |||
Suggested packages: | Suggested packages: | ||
pcmciautils ca-certificates resolvconf | |||
The following NEW packages will be installed: | The following NEW packages will be installed: | ||
easy-rsa libccid liblzo2-2 libpcsclite1 libpkcs11-helper1 libusb-1.0-0 opensc opensc-pkcs11 openssl openvpn pcscd | |||
... | ... | ||
Above'' ''command will also install additional packages, like for example ''easy-rsa'', which we will use to set up our internal ''Certificate Authority'' (CA) infrastructure. | Above'' ''command will also install additional packages, like for example ''easy-rsa'', which we will use to set up our internal ''Certificate Authority'' (CA) infrastructure. | ||
== | == Generating Keys and Certificates - Server == | ||
To encrypt traffic between the server and clients, ''OpenVPN'' utilizes set of certificates and keys. A functional ''OpenVPN'' server requires the following certificates/keys: | To encrypt traffic between the server and clients, ''OpenVPN'' utilizes set of certificates and keys. A functional ''OpenVPN'' server requires the following certificates/keys: | ||
| Line 79: | Line 83: | ||
To configure ''Certificate Authority ''values which will be placed in the certificate, we need to edit the ''/etc/openvpn/rsa/vars'' file and update the following fields: | To configure ''Certificate Authority ''values which will be placed in the certificate, we need to edit the ''/etc/openvpn/rsa/vars'' file and update the following fields: | ||
root@somlabs:/etc/openvpn/rsa# '''vim vars''' | |||
... | ... | ||
export KEY_COUNTRY="US" | export KEY_COUNTRY="US" | ||
export KEY_PROVINCE="CA" | export KEY_PROVINCE="CA" | ||
export KEY_CITY="SanFrancisco" | export KEY_CITY="SanFrancisco" | ||
export KEY_ORG="Fort-Funston" | export KEY_ORG="Fort-Funston" | ||
export KEY_EMAIL="me@myhost.mydomain" | export KEY_EMAIL="me@myhost.mydomain" | ||
export KEY_OU="MyOrganizationalUnit" | export KEY_OU="MyOrganizationalUnit" | ||
... | ... | ||
For example: | For example: | ||
| Line 108: | Line 112: | ||
Let’s finally generate a certificate authority - '''''ca.crt''''' file (druing this process all of the values should be populated automatically from ''vars'' file - just confirm default values): | Let’s finally generate a certificate authority - '''''ca.crt''''' file (druing this process all of the values should be populated automatically from ''vars'' file - just confirm default values): | ||
root@somlabs:/etc/openvpn/rsa# '''./build-ca''' | |||
Generating a 2048 bit RSA private key | Generating a 2048 bit RSA private key | ||
.............................+++ | .............................+++ | ||
..........+++ | ..........+++ | ||
writing new private key to 'ca.key' | writing new private key to 'ca.key' | ||
<nowiki>-----</nowiki> | <nowiki>-----</nowiki> | ||
You are about to be asked to enter information that will be incorporated | You are about to be asked to enter information that will be incorporated | ||
into your certificate request. | into your certificate request. | ||
What you are about to enter is what is called a Distinguished Name or a DN. | What you are about to enter is what is called a Distinguished Name or a DN. | ||
There are quite a few fields but you can leave some blank | There are quite a few fields but you can leave some blank | ||
For some fields there will be a default value, | For some fields there will be a default value, | ||
If you enter '.', the field will be left blank. | If you enter '.', the field will be left blank. | ||
<nowiki>-----</nowiki> | <nowiki>-----</nowiki> | ||
Country Name (2 letter code) [PL]: | Country Name (2 letter code) [PL]: | ||
State or Province Name (full name) [Masovian]: | State or Province Name (full name) [Masovian]: | ||
Locality Name (eg, city) [Warsaw]: | Locality Name (eg, city) [Warsaw]: | ||
Organization Name (eg, company) [SoMLabs]: | Organization Name (eg, company) [SoMLabs]: | ||
Organizational Unit Name (eg, section) [SoMLabs]: | Organizational Unit Name (eg, section) [SoMLabs]: | ||
Common Name (eg, your name or your server's hostname) [SoMLabs CA]: | Common Name (eg, your name or your server's hostname) [SoMLabs CA]: | ||
Name [EasyRSA]: | Name [EasyRSA]: | ||
Email Address [somlabs@somlabs.com]: | Email Address [somlabs@somlabs.com]: | ||
Now generate a server key and certificate ('''''server.crt''''' and '''''server.key''''' files): | Now generate a server key and certificate ('''''server.crt''''' and '''''server.key''''' files): | ||
root@somlabs:/etc/openvpn/rsa# '''./build-key-server server''' | |||
... | |||
Generating a 2048 bit RSA private key | Generating a 2048 bit RSA private key | ||
... | ... | ||
Please enter the following 'extra' attributes | Please enter the following 'extra' attributes | ||
to be sent with your certificate request | to be sent with your certificate request | ||
A challenge password []:'''somlabs''' | A challenge password []:'''somlabs''' | ||
An optional company name []: | An optional company name []: | ||
Using configuration from /etc/openvpn/rsa/openssl.cnf | Using configuration from /etc/openvpn/rsa/openssl.cnf | ||
Check that the request matches the signature | Check that the request matches the signature | ||
Signature ok | Signature ok | ||
The Subject's Distinguished Name is as follows | The Subject's Distinguished Name is as follows | ||
countryName :PRINTABLE:'PL' | countryName :PRINTABLE:'PL' | ||
stateOrProvinceName :PRINTABLE:'Masovian' | stateOrProvinceName :PRINTABLE:'Masovian' | ||
localityName :PRINTABLE:'Warsaw' | localityName :PRINTABLE:'Warsaw' | ||
organizationName :PRINTABLE:'SoMLabs' | organizationName :PRINTABLE:'SoMLabs' | ||
organizationalUnitName:PRINTABLE:'SoMLabs' | organizationalUnitName:PRINTABLE:'SoMLabs' | ||
commonName :PRINTABLE:'server' | commonName :PRINTABLE:'server' | ||
name :PRINTABLE:'EasyRSA' | name :PRINTABLE:'EasyRSA' | ||
emailAddress :IA5STRING:'somlabs@somlabs.com' | emailAddress :IA5STRING:'somlabs@somlabs.com' | ||
Certificate is to be certified until Jun 24 07:08:08 2028 GMT (3650 days) | Certificate is to be certified until Jun 24 07:08:08 2028 GMT (3650 days) | ||
Sign the certificate? [y/n]:y | Sign the certificate? [y/n]:y | ||
1 out of 1 certificate requests certified, commit? [y/n]y | 1 out of 1 certificate requests certified, commit? [y/n]y | ||
Write out database with 1 new entries | Write out database with 1 new entries | ||
Data Base Updated | Data Base Updated | ||
To build a Diffie-Hellman key exchange ('''''dh2048.pem''''' file): | To build a Diffie-Hellman key exchange ('''''dh2048.pem''''' file): | ||
| Line 165: | Line 169: | ||
This is going to take a long time | This is going to take a long time | ||
(it will take some time to generate | (it will take some time to generate the files) | ||
For additional security, user can also generate optional ''Hash-based Message Authentication Code'' - HMAC key ('''''ta.key''''' file): | For additional security, user can also generate optional ''Hash-based Message Authentication Code'' - HMAC key ('''''ta.key''''' file): | ||
| Line 180: | Line 184: | ||
root@somlabs:/etc/openvpn/rsa/keys# cp ta.key /etc/openvpn/server</pre> | root@somlabs:/etc/openvpn/rsa/keys# cp ta.key /etc/openvpn/server</pre> | ||
== | == Generating Keys and Certificates - Client == | ||
In this example we will generate key and certificate pair for one client – you can repeat below steps for each new client, but please remember to set up unique name for all new clients. Please also remember that in production environments - for security purposes – keys should be generated on client machine and signed by the CA machine (it is recommended that the CA machine be separate from the machine running OpenVPN - do not store the ''easy-rsa'' CA files on the OpenVPN server!) – in this example we will generate the signed key on the server: | In this example we will generate key and certificate pair for one client – you can repeat below steps for each new client, but please remember to set up unique name for all new clients. Please also remember that in production environments - for security purposes – keys should be generated on client machine and signed by the CA machine (it is recommended that the CA machine be separate from the machine running OpenVPN - do not store the ''easy-rsa'' CA files on the OpenVPN server!) – in this example we will generate the signed key on the server: | ||
root@somlabs:/etc/openvpn/rsa# '''./build-key client1''' | |||
Generating a 2048 bit RSA private key | Generating a 2048 bit RSA private key | ||
... | ... | ||
writing new private key to 'client1.key' | writing new private key to 'client1.key' | ||
... | ... | ||
Certificate is to be certified until Jun 24 07:39:23 2028 GMT (3650 days) | Certificate is to be certified until Jun 24 07:39:23 2028 GMT (3650 days) | ||
Sign the certificate? [y/n]:y | Sign the certificate? [y/n]:y | ||
1 out of 1 certificate requests certified, commit? [y/n]y | 1 out of 1 certificate requests certified, commit? [y/n]y | ||
Write out database with 1 new entries | Write out database with 1 new entries | ||
Data Base Updated | Data Base Updated | ||
Copy the necessary key files to client, via a secure way (such as SSH), including: | Copy the necessary key files to client, via a secure way (such as SSH), including: | ||
| Line 227: | Line 231: | ||
group nobody</pre> | group nobody</pre> | ||
As | As an option, you can uncomment: | ||
push "redirect-gateway def1 bypass-dhcp" | push "redirect-gateway def1 bypass-dhcp" | ||
| Line 235: | Line 239: | ||
To start OpenVPN server: | To start OpenVPN server: | ||
root@somlabs:/etc/openvpn# '''openvpn /etc/openvpn/server.conf''' | |||
... | ... | ||
Wed Jun 27 08:04:19 2018 TUN/TAP device tun0 opened | Wed Jun 27 08:04:19 2018 TUN/TAP device tun0 opened | ||
Wed Jun 27 08:04:19 2018 TUN/TAP TX queue length set to 100 | Wed Jun 27 08:04:19 2018 TUN/TAP TX queue length set to 100 | ||
Wed Jun 27 08:04:19 2018 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 | Wed Jun 27 08:04:19 2018 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 | ||
Wed Jun 27 08:04:19 2018 /sbin/ip link set dev tun0 up mtu 1500 | Wed Jun 27 08:04:19 2018 /sbin/ip link set dev tun0 up mtu 1500 | ||
... | ... | ||
Wed Jun 27 08:04:19 2018 UDPv4 link remote: [AF_UNSPEC] | Wed Jun 27 08:04:19 2018 UDPv4 link remote: [AF_UNSPEC] | ||
Wed Jun 27 08:04:19 2018 GID set to nogroup | Wed Jun 27 08:04:19 2018 GID set to nogroup | ||
Wed Jun 27 08:04:19 2018 UID set to nobody | Wed Jun 27 08:04:19 2018 UID set to nobody | ||
Wed Jun 27 08:04:19 2018 MULTI: multi_init called, r=256 v=256 | Wed Jun 27 08:04:19 2018 MULTI: multi_init called, r=256 v=256 | ||
Wed Jun 27 08:04:19 2018 IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0 | Wed Jun 27 08:04:19 2018 IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0 | ||
Wed Jun 27 08:04:19 2018 IFCONFIG POOL LIST | Wed Jun 27 08:04:19 2018 IFCONFIG POOL LIST | ||
Wed Jun 27 08:04:19 2018 '''Initialization Sequence Completed''' | Wed Jun 27 08:04:19 2018 '''Initialization Sequence Completed''' | ||
To connect to the ''OpenVPN'' server, the client requires a key and certificate that we created already: | To connect to the ''OpenVPN'' server, the client requires a key and certificate that we created already: | ||
| Line 285: | Line 289: | ||
[4] [https://wiki.archlinux.org/index.php/OpenVPN https://wiki.archlinux.org/index.php/OpenVPN] | [4] [https://wiki.archlinux.org/index.php/OpenVPN https://wiki.archlinux.org/index.php/OpenVPN] | ||
== Ready to use image file == | |||
You can also use a prepared image file. | |||
You need to download the image file: | |||
[http://ftp.somlabs.com/VisionSOM-6ULL/SoMLabs-VisionSOM-6ULL-OpenVPN.zip SoMLabs-VisionSOM-6ULL-OpenVPN.zip] | |||
Then you need to write the image file to microSD card. More information you can find in manuals: [[How to prepare SD Card with Debian 9.2 for VisionSOM-6ULL on Linux]] or [[How to prepare SD Card with Debian 9.2 for VisionSOM-6ULL on Windows]]. | |||
For testing purposes user '''root''' has a password '''somlabs'''. | |||
Latest revision as of 11:57, 11 July 2018
OpenVPN and VisionSOM-6ULL
OpenVPN [1] is an open-source software application that implements virtual private network (VPN) techniques to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. In other words, OpenVPN allows you to create a private network over the public Internet and tunnels your network connection securely. This tutorial describes the steps to setup the OpenVPN server on VisionSOM-6ULL module.
Prerequisites
This tutorial is based on a pre-prepared image for VisionSOM-6ULL module. The image is available here: SoMLabs-VisionSOM-6ULL-OpenVPN.zip.
For testing purposes user root has a password somlabs.
Then you need to write the image file to microSD card. More information you can find in manuals: How to prepare SD Card with Debian 9.2 for VisionSOM-6ULL on Linux or How to prepare SD Card with Debian 9.2 for VisionSOM-6ULL on Windows. Please remember to use a proper image file: SoMLabs-VisionSOM-6ULL-OpenVPN.zip.
Kernel configuration – TUN/TAP device support
OpenVPN requires TUN/TAP (CONFIG_TUN) device support. The source of this driver is already included in the Linux kernel for SoMLabs module, but driver is not selected by default. To enable support for Universal TUN/TAP device, please configure kernel with menuconfig tool:
cd <linux-sources> make ARCH=arm menuconfig
and choose the right driver:
Device Drivers --->
<*> Network device support --->
[*] Network core driver support
<*> Universal TUN/TAP device driver support
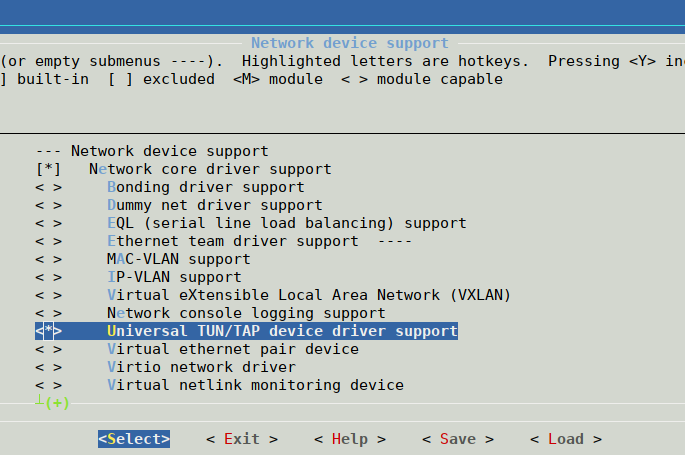
After all these options have been selected, save your configuration, exit the menuconfig tool and build a new kernel image:
make ARCH=arm zImage
In last steps, transfer the new kernel images to a microSD:
sudo mount /dev/sdbX /mnt/sdcard cd /mnt/sdcard sudo cp <linuxsources>/arch/arm/boot/zImage boot/
and boot SoMLabs module form SD card.
OpenVPN software installation
OpenVPN package – which is available in Debian's default repositories - provides both server and client mode. To update server's package repository and install openvpn software:
root@somlabs:~# apt-get update root@somlabs:~# apt-get install openvpn Reading package lists... Done Building dependency tree Reading state information... Done The following additional packages will be installed: easy-rsa libccid liblzo2-2 libpcsclite1 libpkcs11-helper1 libusb-1.0-0 opensc opensc-pkcs11 openssl pcscd Suggested packages: pcmciautils ca-certificates resolvconf The following NEW packages will be installed: easy-rsa libccid liblzo2-2 libpcsclite1 libpkcs11-helper1 libusb-1.0-0 opensc opensc-pkcs11 openssl openvpn pcscd ...
Above command will also install additional packages, like for example easy-rsa, which we will use to set up our internal Certificate Authority (CA) infrastructure.
Generating Keys and Certificates - Server
To encrypt traffic between the server and clients, OpenVPN utilizes set of certificates and keys. A functional OpenVPN server requires the following certificates/keys:
- CA's public certificate (ca.crt file),
- server public certificate (in this example - server.crt file),
- server public key (in this example - server.key file),
- the Diffie-Hellman (DH) parameters file (dh2048.pem file),
To protecting against portscanning, DOS attacks and any eventual buffer overflow vulnerabilities, user can also generate optional Hash-based Message Authentication Code - HMAC key (ta.key file).
To issue trusted certificates, the first step when setting up OpenVPN is creation our own simple Certificate Authority (CA) with easy-rsa tool. As a first, we need to create a new /etc/openvpn/rsa directory for generated keys and certificates:
root@somlabs:~# mkdir /etc/openvpn/rsa
and copy the key and certificate generation scripts into new directory:
root@somlabs:~# cp -rf /usr/share/easy-rsa/* /etc/openvpn/rsa
Because easy-rsa tool cannot find /etc/openvpn/rsa/openssl.cnf file on Debian 9 “Stretch” Linux Systems, we need to create symbolic symlink before we run generation scripts:
root@somlabs:~# cd /etc/openvpn/rsa/ root@somlabs:/etc/openvpn/rsa# ln -s openssl-1.0.0.cnf openssl.cnf
To configure Certificate Authority values which will be placed in the certificate, we need to edit the /etc/openvpn/rsa/vars file and update the following fields:
root@somlabs:/etc/openvpn/rsa# vim vars ... export KEY_COUNTRY="US" export KEY_PROVINCE="CA" export KEY_CITY="SanFrancisco" export KEY_ORG="Fort-Funston" export KEY_EMAIL="me@myhost.mydomain" export KEY_OU="MyOrganizationalUnit" ...
For example:
export KEY_COUNTRY="PL" export KEY_PROVINCE="Masovian" export KEY_CITY="Warsaw" export KEY_ORG="SoMLabs" export KEY_EMAIL="somlabs@somlabs.com" export KEY_OU="SoMLabs"
At this point we are ready to build our CA root. As a first, source the vars file:
root@somlabs:/etc/openvpn/rsa# source ./vars
and clean CA root environment:
root@somlabs:/etc/openvpn/rsa# ./clean-all
Let’s finally generate a certificate authority - ca.crt file (druing this process all of the values should be populated automatically from vars file - just confirm default values):
root@somlabs:/etc/openvpn/rsa# ./build-ca Generating a 2048 bit RSA private key .............................+++ ..........+++ writing new private key to 'ca.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [PL]: State or Province Name (full name) [Masovian]: Locality Name (eg, city) [Warsaw]: Organization Name (eg, company) [SoMLabs]: Organizational Unit Name (eg, section) [SoMLabs]: Common Name (eg, your name or your server's hostname) [SoMLabs CA]: Name [EasyRSA]: Email Address [somlabs@somlabs.com]:
Now generate a server key and certificate (server.crt and server.key files):
root@somlabs:/etc/openvpn/rsa# ./build-key-server server ... Generating a 2048 bit RSA private key ... Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:somlabs An optional company name []: Using configuration from /etc/openvpn/rsa/openssl.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'PL' stateOrProvinceName :PRINTABLE:'Masovian' localityName :PRINTABLE:'Warsaw' organizationName :PRINTABLE:'SoMLabs' organizationalUnitName:PRINTABLE:'SoMLabs' commonName :PRINTABLE:'server' name :PRINTABLE:'EasyRSA' emailAddress :IA5STRING:'somlabs@somlabs.com' Certificate is to be certified until Jun 24 07:08:08 2028 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
To build a Diffie-Hellman key exchange (dh2048.pem file):
root@somlabs:/etc/openvpn/rsa# ./build-dh Generating DH parameters, 2048 bit long safe prime, generator 2 This is going to take a long time
(it will take some time to generate the files)
For additional security, user can also generate optional Hash-based Message Authentication Code - HMAC key (ta.key file):
root@somlabs:/etc/openvpn/rsa# openvpn --genkey --secret keys/ta.key
At this point we have generated all required certificates/keys for server instance (all generated files were placed within the /etc/openvpn/rsa/keys directory) - let’s move them to /etc/openvpn/server:
root@somlabs:~# cd /etc/openvpn/rsa/keys/ root@somlabs:/etc/openvpn/rsa/keys# cp ca.crt /etc/openvpn/server root@somlabs:/etc/openvpn/rsa/keys# cp server.crt /etc/openvpn/server root@somlabs:/etc/openvpn/rsa/keys# cp server.key /etc/openvpn/server root@somlabs:/etc/openvpn/rsa/keys# cp dh2048.pem /etc/openvpn/server root@somlabs:/etc/openvpn/rsa/keys# cp ta.key /etc/openvpn/server
Generating Keys and Certificates - Client
In this example we will generate key and certificate pair for one client – you can repeat below steps for each new client, but please remember to set up unique name for all new clients. Please also remember that in production environments - for security purposes – keys should be generated on client machine and signed by the CA machine (it is recommended that the CA machine be separate from the machine running OpenVPN - do not store the easy-rsa CA files on the OpenVPN server!) – in this example we will generate the signed key on the server:
root@somlabs:/etc/openvpn/rsa# ./build-key client1 Generating a 2048 bit RSA private key ... writing new private key to 'client1.key' ... Certificate is to be certified until Jun 24 07:39:23 2028 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
Copy the necessary key files to client, via a secure way (such as SSH), including:
- /etc/openvpn/easy-rsa/keys/ca.crt,
- /etc/openvpn/easy-rsa/keys/client1.crt,
- /etc/openvpn/easy-rsa/keys/client1.key,
- /etc/openvpn/easy-rsa/keys/ta.key (if using tls-auth).
Configure the OpenVPN Service
The OpenVPN package comes with set of example configuration files which are an ideal starting point for a basic OpenVPN server setup with the following features:
- uses Public Key Infrastructure for authentication,
- creates a VPN using a virtual TUN network interface,
- listens for client connections on UDP port 1194,
- distributes virtual addresses to connecting clients from the 10.8.0.0/24 subnet.
To prepare such basic server setup, copy and unzip a sample OpenVPN configuration file into configuration directory:
root@somlabs:~# gunzip -c /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz > /etc/openvpn/server/server.conf
Edit the /etc/openvpn/server/server.conf file making a minimum of the following changes:
... ca ca.crt cert server.crt key server.key dh dh2048.pem ... user nobody group nobody
As an option, you can uncomment:
push "redirect-gateway def1 bypass-dhcp"
line to redirect all traffic through our OpenVPN. For more advanced configurations, please see OpenVPN documentation [2].
To start OpenVPN server:
root@somlabs:/etc/openvpn# openvpn /etc/openvpn/server.conf ... Wed Jun 27 08:04:19 2018 TUN/TAP device tun0 opened Wed Jun 27 08:04:19 2018 TUN/TAP TX queue length set to 100 Wed Jun 27 08:04:19 2018 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Wed Jun 27 08:04:19 2018 /sbin/ip link set dev tun0 up mtu 1500 ... Wed Jun 27 08:04:19 2018 UDPv4 link remote: [AF_UNSPEC] Wed Jun 27 08:04:19 2018 GID set to nogroup Wed Jun 27 08:04:19 2018 UID set to nobody Wed Jun 27 08:04:19 2018 MULTI: multi_init called, r=256 v=256 Wed Jun 27 08:04:19 2018 IFCONFIG POOL: base=10.8.0.4 size=62, ipv6=0 Wed Jun 27 08:04:19 2018 IFCONFIG POOL LIST Wed Jun 27 08:04:19 2018 Initialization Sequence Completed
To connect to the OpenVPN server, the client requires a key and certificate that we created already:
- /etc/openvpn/easy-rsa/keys/ca.crt,
- /etc/openvpn/easy-rsa/keys/client1.crt,
- /etc/openvpn/easy-rsa/keys/client1.key,
- /etc/openvpn/easy-rsa/keys/ta.key (if using tls-auth).
Copy the above files to client device (with OpenVPN client software) and afterwards create a new file called for client.ovpn with minimal configuration (like below):
client dev tun proto udp remote <openvpn server IP> 1194 resolv-retry infinite nobind persist-key persist-tun comp-lzo verb 3 ca ca.crt cert client1.crt key client1.key
Please remember that your network infrastructure with OpenVPN server may need additional configuration – please check out your firewall, port forwarding and iptables settings in case of any troubles.
At this point you should be ready to enable traffic routing to OpenVPN server. For more info please visit:
[2] https://openvpn.net/index.php/open-source/documentation
[3] https://help.ubuntu.com/community/OpenVPN
[4] https://wiki.archlinux.org/index.php/OpenVPN
Ready to use image file
You can also use a prepared image file.
You need to download the image file: SoMLabs-VisionSOM-6ULL-OpenVPN.zip
Then you need to write the image file to microSD card. More information you can find in manuals: How to prepare SD Card with Debian 9.2 for VisionSOM-6ULL on Linux or How to prepare SD Card with Debian 9.2 for VisionSOM-6ULL on Windows.
For testing purposes user root has a password somlabs.